How can law firms and companies best protect their most critical infrastructure: the IT systems and networks that are the backbone of those organisations?
Today, law firms and companies are subject to an array of cybersecurity risks, some predictable and some not, which can sharply impact their value, reputation, and functionality. In some cases, cyber-attacks can threaten the Information Technology (IT) infrastructure of an organisation with an outright collapse.
Strengthening cybersecurity is difficult, and advanced technologies such as the internet of things and the metaverse will inevitably make things worse. Indeed, a world in which more objects are computerised and digitised is a world with more targets for cyber-criminals. Even more concerning is the unpredictability of cyber-attacks that can trigger cascading network and system failures that are well beyond existing cybersecurity policies or strategies. Not surprisingly then, the Securities and Exchange Commission proposed in March rules for companies to periodically disclose their cybersecurity risk management policies and strategy.
However, as T.S. Eliot wrote, “Between the idea and the reality falls the shadow.” In other words, the gap between theory and practice can be wide.
Law firms and companies do not lack strategies or ideas for strengthening their cybersecurity policies; however, many lack practical guidance on how to effectively implement these policies and put them into practice. Strengthening cybersecurity standards extends beyond installing firewalls. Indeed, one of the most effective countermeasures with which to avert cyber-threats is to implement robust strategies, procedures, and standards that can protect an organisation’s critical IT infrastructure while aligning with its business objectives or operational mission.
Creating a resilient cybersecurity framework
As cyber-attacks have become more sophisticated, the need to create a resilient cybersecurity framework has grown. Indeed, according to the UK’s Cyber Security Breaches Survey 2022, 39% of UK businesses said they were victims of cyber-attacks within the past 12 months.
Faced with this picture, it is natural to worry most about the range of risks caused by cyber-attacks. Yet, despite these worries, these risks can be managed. In this sense, a law firm or company must broaden its cybersecurity strategy by implementing effective countermeasures in order to create a resilient cybersecurity framework. This involves a thorough analysis of the critical components of an organisation’s virtual ecosystem as well as identifying what could happen if any of the critical components failed or became compromised.
A law firm or company also should consider and identify the critical components of its overall computing environment and consider how each component interacts with one another. The aim is to ensure that it can identify the weakest link in its current computing environment framework by locating a weak component at an early stage and building an effective response to manage and mitigate potential attacks to its overall digital infrastructure.
Once a weak component is located and identified, it is paramount to assess what relevant cybersecurity policies and strategies need to be implemented in order the strengthen the weak component and achieve an overall secure computing environment framework. Equally important, organisations should establish which of their professionals is responsible for paying attention to the operation and security of the organisation’s essential components — and this demands a top-down management approach. Senior managers and decision-makers should understand the driving force behind the development of an enhanced cybersecurity framework and establish a strong information security program that aligns with the organisation’s business objectives.
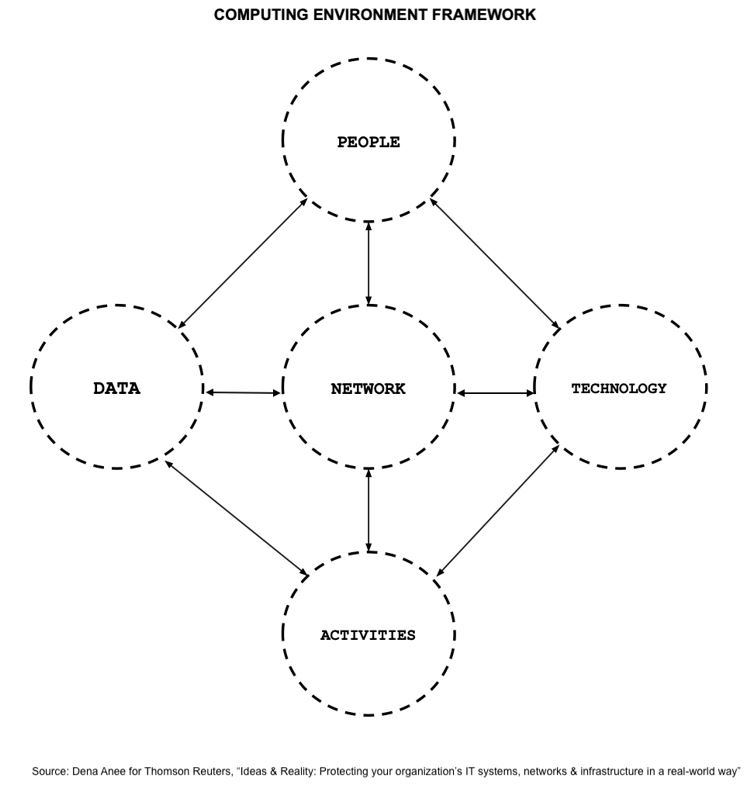
One such measure would be for the organisation to create a cybersecurity strategy that captures the conditions that are required for creating a cyber resilient environment. Demonstrating strength in some of the following areas is one way of creating effective countermeasures:
- Establishing well-defined processes and recovery plans to ensure the ability to fully recover and restore IT systems with minimal outage times.
- Training employees on how they can perform their work responsibilities in a way that is able to preserve the confidentiality and integrity of sensitive data as well as encouraging employees to enhance security through vigilance and collaboration.
- Ensuring that IT systems and networks are up-to-date and able to keep pace with ever-evolving cybersecurity threats.
Further, implementing the type of cybersecurity standards defined by the International Organisation for Standardisation can also be an effective tool with which to protect an organisation’s IT systems and sensitive data and mitigate the risks of cyber-attacks. For example, one such standard can form a blueprint for organisations to implement the necessary procedures, policies, and framework to manage a law firm’s or a company’s information security, cybersecurity, and privacy protection; another allows organisations to protect its storage, processing, and transmission of cardholder data. In fact, that standard specifies 12 operational and technical requirements that can help organisations prevent credit card fraud and maintain a secure environment for its customers.
In today’s increasingly interconnected world, where people, goods, and services move across borders, it is paramount that organisations respond to cyber-threats in a timely and effective fashion in order to protect their most critical components and to contain, prevent, and shield their most important data from being attacked, stolen, or compromised. In order to best protect their IT systems, networks, and infrastructure, law firms and companies must define, develop, and implement robust cybersecurity strategies and procedures that can achieve the right balance between concern and action.
This article first featured on Thomson Reuters Institute, and has been republished with full permission.


